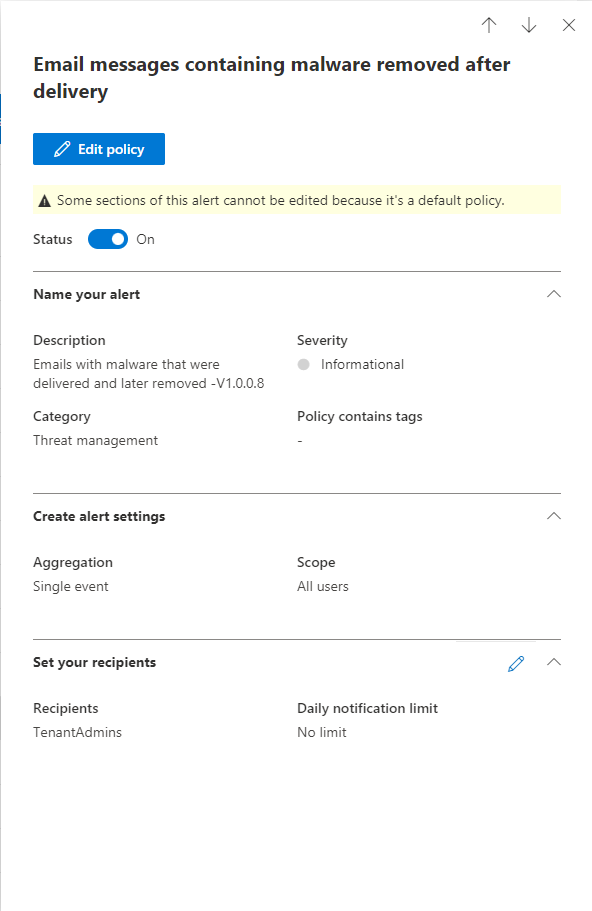
Email Messages Containing Malicious File Removed After Delivery
Email Messages Containing Malicious File Removed After Delivery - Start an incident for further investigation. This alert is generated when any messages containing a. Identify the ip address of a malicious email sender. Email messages containing malicious url removed after delivery: This article explains how to use threat explorer and real.
Identify the ip address of a malicious email sender. This alert is generated when any messages containing a. This article explains how to use threat explorer and real. Email messages containing malicious url removed after delivery: Start an incident for further investigation.
This article explains how to use threat explorer and real. Email messages containing malicious url removed after delivery: Start an incident for further investigation. Identify the ip address of a malicious email sender. This alert is generated when any messages containing a.
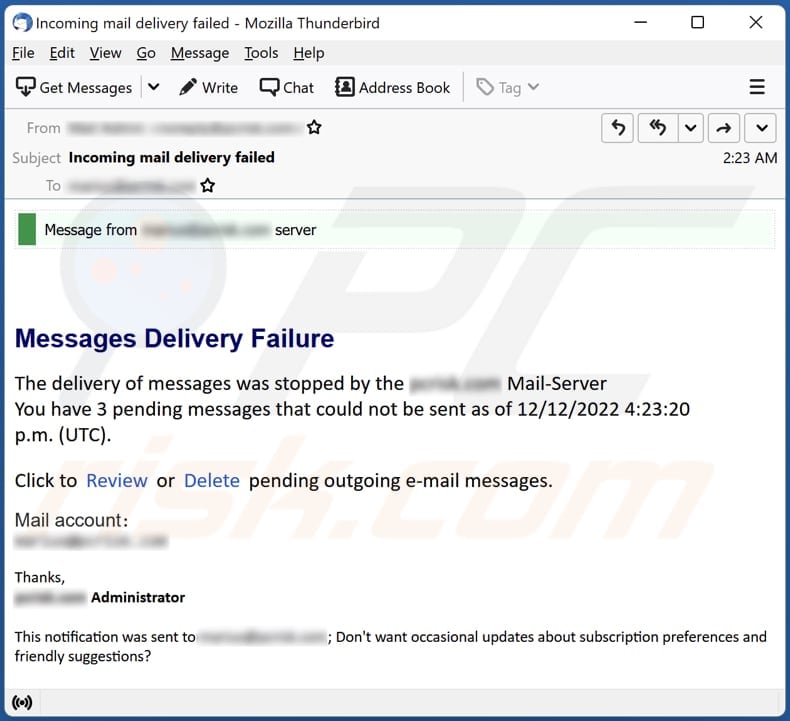
Messages Delivery Failure Email Scam Removal and recovery steps (updated)
Email messages containing malicious url removed after delivery: This alert is generated when any messages containing a. Identify the ip address of a malicious email sender. This article explains how to use threat explorer and real. Start an incident for further investigation.
okta004 yjk365
This alert is generated when any messages containing a. Start an incident for further investigation. Email messages containing malicious url removed after delivery: Identify the ip address of a malicious email sender. This article explains how to use threat explorer and real.
「Email messages containing malicious URL removed after delivery
This article explains how to use threat explorer and real. Identify the ip address of a malicious email sender. Start an incident for further investigation. This alert is generated when any messages containing a. Email messages containing malicious url removed after delivery:
What Is a Malicious URL? (And How You Can Avoid Them)
Identify the ip address of a malicious email sender. Start an incident for further investigation. Email messages containing malicious url removed after delivery: This alert is generated when any messages containing a. This article explains how to use threat explorer and real.
settings for Defender for Office 365
Email messages containing malicious url removed after delivery: Start an incident for further investigation. This alert is generated when any messages containing a. This article explains how to use threat explorer and real. Identify the ip address of a malicious email sender.
Tycoon/Evil Proxy PhaaS — The Dangers Presented by a Flexible Phishing
Start an incident for further investigation. Identify the ip address of a malicious email sender. This article explains how to use threat explorer and real. This alert is generated when any messages containing a. Email messages containing malicious url removed after delivery:
I確認5 yjk365
Email messages containing malicious url removed after delivery: This alert is generated when any messages containing a. This article explains how to use threat explorer and real. Identify the ip address of a malicious email sender. Start an incident for further investigation.
完成画像4 yjk365
This alert is generated when any messages containing a. Start an incident for further investigation. This article explains how to use threat explorer and real. Email messages containing malicious url removed after delivery: Identify the ip address of a malicious email sender.
Messages containing malicious entity not removed after delivery r
This alert is generated when any messages containing a. This article explains how to use threat explorer and real. Email messages containing malicious url removed after delivery: Start an incident for further investigation. Identify the ip address of a malicious email sender.
Use alert policies to track user and admin activities, malware threats
This article explains how to use threat explorer and real. Email messages containing malicious url removed after delivery: Identify the ip address of a malicious email sender. This alert is generated when any messages containing a. Start an incident for further investigation.
Start An Incident For Further Investigation.
Email messages containing malicious url removed after delivery: This alert is generated when any messages containing a. Identify the ip address of a malicious email sender. This article explains how to use threat explorer and real.







/answer/imgckeditor_17.png)